An exploration of the architectural requirements for implementing robust technologies in e-government scenarios.
- Version
-
v1.0, 2023-09-30 (Leipzig)
- Editors
-
Florian Gudat
Maja Katharina Hoffmann
Sergi Domenech Guzy - Module
-
Project C149.2 Compulsory module
- Module Supervisor
-
Prof. Dr. Thomas Riechert
- Lecturer
-
Prof. Dr. Andreas Both
- Institute
-
Leipzig University of Applied Sciences
- Faculty
-
Computer Science and Media
- Abstract
-
Amidst data protection incidents and IT security breaches, it is crucial that web application processed data remains secure from unauthorised access. In addressing this issue, Tim-Berners Lee started the Solid initiative, which facilitates storage and processing of data in a decentralised network. This project serves as a showcase of citizen data storage and processing in the context of public administration processes using Solid principles.
Table of Contents
1. Motivation
Navigating public services is a task every German citizen is confronted regularly. Often, public service processes, such as submitting a tax declaration, require citizens to provide additional data, which itself needs to be obtained from other public offices. A recent change in German property tax law required all citizens who are property owners in Germany to submit a property tax declaration, based on which tax rates for the following years would be calculated. The form for this declaration also required property owners to obtain property data from the local land registry office and provide it as an attachment to the property tax declaration. This resulted in a lengthy process, which is still ongoing.
Offering public services digitally can facilitate the navigation of processes for citizens. Additionally, if personal or public service data is available digitally, communication between offices can be streamlined, reducing the effort needed on behalf of citizens to provide data. Enhancing digital data processing for public service has been extensively discussed in Germany in recent years. Despite some advancements, such as the Onlinezugangsgesetz that aimed to provide 575 public administration services digitally, their ambition remains unfulfilled. As of 2023, only 132 services are comprehensively available throughout Germany [1].
One of the challenges in providing digitally available public services is ensuring data protection and privacy. If personal data concerning a citizen is produced and maintained by one public office, this data cannot be shared with other parties, even if it is needed for an official process. This places responsibility for obtaining information from secondary public offices with the citizens, which leads to reduced efficiency, since navigating service offices can be time-consuming.
A parallel technological advancement is the Solid specification, a decentralised and secure storage solution that has been under development by the Solid Community Group since 2018. Additionally, this approach is based on publicly defined schemas, open to all.
As these specifications aim to provide solutions for problems similar to those described previously, the applicability of the specification for German public authorities should be examined. Following an agreed upon set of standards and specifications, each office can develop their IT infrastructure at their own pace while ensuring compatibility of produced data types.
The situation described leads to the following key research question this paper aims to address:
-
Is the Solid technology suitable for a naive e-government solution, or does it require additional specifications to serve as an approach for the development of e-government applications?
In this context, we refer to solutions proposed in this work as naive, since they were developed focusing only on the citizen as a user. As a result, complicated data processing and government business logic are excluded, and only the storage, access and submission of citizen data is covered.
Various concerns need to be considered in the development of e-government applications, such as interoperability, i.e. the compatibility of produced data, privacy and data sovereignty, as well as usability.
Therefore, the key research question can be divided into multiple essential questions to be answered:
-
Does the Solid specification cover all the requirements of a government process?
-
Which currently available reference implementations of the specifications can be used in development?
-
Which processes and data flows need to be modelled in applications to facilitate interoperability?
-
Is the protection of citizens' data and sovereignty ensured by the technology used?
-
Can applications build based on these specifications offer an improvement in usability compared to current processes?
To answer these questions, in this work we will formulate requirements for e-government applications based on common scenarios. Based on these requirements, we will implement a showcase scenario with multiple applications. Applications in this showcase will be built on the specifications developed by the Solid Community Group and use current available reference implementations. We will discuss the implementation strategies and decisions needed in development and evaluate which further insights can be derived from our work.
2. Theoretical Foundations
In this section, we will describe and define the theoretical foundations and frameworks pertinent to the project to establish a uniform understanding of the terminology used. We outline e-governance as a technical domain and data sovereignty as a result of the context. Additionally, we consider Solid as a technological basis.
2.1. E-Governance
E-government allows citizens and businesses to access state services in a convenient and flexible manner, independent of time restrictions [13].
2.2. Data Sovereignty
The term data sovereignty is used in various contexts and often carries different meanings. A universally agreed-upon definition doesn’t exist. Its literal significance implies control over data, its storage, collection, and processing. Interpreted this way, data sovereignty can indicate an individual’s control over their entitled data or data concerning them [2].
For the purposes of this research, control of personal data is described as safeguarding against unauthorised access and limiting access to only authorised individuals. Subsequently, data sovereignty is defined, within the following context, by the provisions of the General Data Protection Regulation (GDPR), which establishes a standard for all digital entities operating in Europe. The following principles of data protection are particularly relevant to this showcase:
- [GDPR-1]
-
"Lawfulness, fairness and transparency — Processing must be lawful, fair, and transparent to the data subject" [3].
- [GDPR-2]
-
"Purpose limitation — You must process data for the legitimate purposes specified explicitly to the data subject when you collected it" [3].
- [GDPR-3]
-
"Data minimisation — You should collect and process only as much data as absolutely necessary for the purposes specified" [3].
Other provisions of the GDPR not relevant to the research interest are disregarded in this showcase. If the web service is intended to run in a productive environment, all required provisions must be met [3].
2.3. Solid
Solid (Social Linked Data) is a set of technological specifications for the exchange of social data that is built on a number of pre-existing standards. It includes technologies for communication, data management and security. The central idea of the Solid project is to provide interoperable standards and "fundamental affordances for decentralised Web applications for information exchange in a way that is secure and privacy respecting. In this environment, actors allocate identifiers for their content, shape and store data where they have access to, set access controls, and use preferred applications and services to achieve them" [4].
Due to the abundance of associated information, only the core concepts are presented here, supplemented by selected parts of the specification.
|
Note
|
Since all specifications are still in development, some of the terminology is still subject to changes. |
2.3.1. Terminology
This document uses the terms storage, Solid app, URI, resource, agent and owner as defined in the Solid Protocol [5]. In addition, the terms RDF, RDF vocabulary, and namespace prefix from RDF 1.1 Concepts and Abstract Syntax [6] are used. Turtle is used as defined in RDF 1.1 Turtle [7]. The meaning of WebID is defined in WebID 1.0 [8]. The use of the Access Control List (ACL) resource and access mode is defined in Web Access Control [9], while Access Control Policy (ACP) is defined in its specification [10]. The term Access Requests and Grants is used as defined in Access Requests and Grants [11].
The following terms will extend the definitions above.
- Data Trustee
-
A data trustee is an independent identity of trust that mediates data between the data provider and the data user in a secure and legally compliant manner [12].
- Enterprise Solid Server (ESS)
-
The Enterprise Solid Server (ESS) is a Solid implementation developed by Inrupt, Inc..
This is not an exhaustive list of the entire terminology used in Solid. For information about associated technologies, please consult the Solid Technical Reports or the Inrupt Documentation.
2.3.2. About Solid
The Solid architecture comprises identities, storage, servers and Solid apps. The storage or Solid Pod functions as a secure data vault. Any data can be stored in a storage, as long as it is compatible with the Linked Data specifications. Solid servers, either self-hosted or as a provider, are responsible for managing user identity along with any data stored in storages, including regulating access to this data. Solid applications are able to utilize and manipulate data stored in storages as long as the required permissions have been granted by the data storage owner. The fundamental premise of the Solid project is to work towards a decentralised World Wide Web with federated systems, where users have control and access to all their personal data. Any user can have a data storage linked to their identity at any location or server. Data from the storage can be employed in applications designed to operate with the Solid specification. Data can be shared with applications or other users, and access control can be achieved. These standards enable the creation of federated systems where data is arranged in a decentralised manner. For more information on Solid, please refer to the About Solid Website.
3. Previous Research
Since the Solid project has started, and the first demonstration of a Social Application using the Solid specifications has been published [14], there have been a number of attempts to apply the ideas to different domains.
Zhao et al. [15] demonstrated a way to shard public transportation data through a Solid framework. Werbrouck et al. [16] showed an application to access common data shared in construction processes and identified the Solid specifications as a useful way to adapt Linked Data principles in the domain of Building Information Modeling (BIM). Henselmann et al. [17] applied the Solid specifications to a loan request use case, showing that Solid can be useful in a B2B or B2C context. Some research has been made on the use of Solid specifications in the healthcare domain. Weng et al. [18] proposed a cloud data model based on Solid for the storing of personal health data and Chen et al. [19] used Solid Pods as storage for wearable medical devices.
In "Making Sense of Solid for Data Governance and GDPR" [20], a theoretical exploration of Solid in the context of GDPR regulations, the authors describe a lack of features in current Solid specifications, given the compliance obligations and enforcement as envisioned by GDPR. However, Sun et al. [21] and Bailly et al. [22] investigated the development of Solid applications under the GDPR, focused on personal health data and general personal data, respectively. The latter especially explored the difficulties in UI design that arise, when combining the conceptual requirements of both interoperability and data privacy restrictions. This is mirrored by a survey [23] done by the SolidLab Flanders, in which 12 people with experience in designing Solid applications have identified difficulties in explaining the main concepts of Solid to users as the biggest challenge.
As pointed out by Penteado et al. [24] the biggest challenge in providing government data in a Linked Data structure is still that there are no uniform processes yet, even though linked open data offers a lot of useful advantages.
4. Scenario, Requirements and Concept
This section outlines the scenario which involves an electronically supported process, the assumed requirements resulting from the technical basis and the general concept.
4.1. Scenario
Germany has a federal system of governance, which results in multiple public authorities with distinctive responsibilities and duties towards citizens. The interaction between citizens and the authorities occurs through bureaucratic procedures like application forms. These forms frequently require data from other public authorities, the private sector or other recurring data that has to be specified again each time. This has led to considerable frustration among citizens, especially in the current age of digital data. An exemplary case of this frustration was the Erklärung zur Feststellung des Grundsteuerwerts 2022 [25].
Grundsteuer (property tax) is charged on real estate by the German government and is the responsibility of the property owners to pay. As of 2022, citizens were required to submit a new declaration containing their property details to ensure that their tax calculations were accurate. However, the authorities had much of the information needed to make the declaration, such as Lage des Grundstücks, Grundstücksfläche, Bodenrichtwert, Gebäudeart Wohnfläche, and Baujahr des Gebäudes _. The main problem is that the data was managed by different authorities, namely the _Finanzämter, the Katasteramt and the Grundbuchamt. As there has been no opportunity to share or access the existing data, it was necessary to declare it again [25], [26]. (The information may vary, as the regulations and names of the offices are not standardized in the Germany.)
To summarise, there are two possible solutions that could improve interactions with public authorities. Users should be able to share or access data from public authorities to others if they are authorised for it, without having to obtain and manage it themselves. For future use of the data, it is essential to ensure accuracy and immutability once declared.
4.2. Requirements
Based on the previously described foundations for data processing maintaining the data sovereignty of users, we developed these requirements.
- [REQ-1]
-
Users must be able to provide clear consent for the processing of their personal data, as outlined in [GDPR-1]. To achieve this, the application’s user interface should clearly present each access requirement to the user and detail which data will be accessed and what rights will be granted to applications, as demanded in [GDPR-3].
- [REQ-2]
-
Applications must allow interoperability, by utilising the same data and offering easy ways to pass data between applications, as described in Scenario.
- [REQ-3]
-
Applications should not require deep understanding of underlying technologies on the user side, as E-Governance applications should be convenient and easy to use.
- [REQ-4]
-
To minimise the effort required to maintain data and to avoid errors, it is proposed not to require users to store all relevant data in their individual storages, as shown in the Scenario.
- [REQ-5]
-
After a user submitted a form at a government office, they should have access to that data, but not be able to change it after the submission, as illustrated by the given Scenario.
- [REQ-6]
-
Applications will only request access to a user’s data if it is necessary according to the demands of [GDPR-2].
4.3. Concept
As a concept for this showcase, we propose a network of multiple applications to provide e-governance processes for citizens. Two distinct types of applications are required, along with a data storage system used by these applications. This data storage holds personal data, either directly under the control of the citizen or managed by government offices.
To give citizens complete control over their personal data, we propose the citizen application as the first type of application. This application allows direct access and editing of all personal data. Moreover, when used with other applications, it provides supplementary functions such as communication via messages or data access management.
For e-governance processes, we propose the second type of application, the government applications, each of which fulfils the role of a single public administration service.
Stored personal data, sourced from different agents, can be shared between these government applications, creating a network of interdependent applications.
These government applications enable e-governance functionality and allow citizens to interact with government services, such as providing personal information and creating new personal data, utilising existing data.
In subsequent diagrams, government applications and their corresponding storages are denoted by OfficeNApplication and OfficeNStorage respectively, to differentiate between multiple government applications.
5. Implementation
This section focuses on the technical implementation of the macro architecture and network of web applications, along with their interaction. Additionally, we examine the modelling of data, emphasizing ownership (whether by the owner or trustee) and the resulting access permissions. Lastly, we present selected scenarios and processes used to resolve specific issues within the macro architecture.
5.1. Architecture
Before examining the specific applications, it is imperative to discuss the essential identities, which are the unique system-wide identifiers of the agents, as derived from the Concept. The primary concerns are the citizen and the government, with the government serving as a representative of any institution listed in Applications. These objects are identified based on the requirements and Solid technology and can be obtained from the figure below.
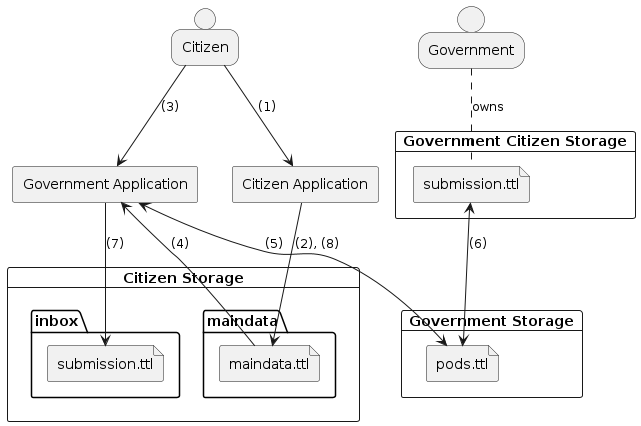
The figure illustrates the essential entities required for the programmatic process, with third-party services, such as the identity provider, excluded in this depiction. These entities include the applications and data storages that correspond to the agents. Furthermore, the government application includes an additional storage that safeguards the citizen’s data.
The numbered directional arrows depict a possible data flow path between the various components and their ranking in the flow. The diagram also indicates relationships between the components with dashed arrows.
5.2. Technologies
When considering the technology used, certain prerequisites affect technological decisions. Solid is built on web technologies, which establishes a web-based architecture as the overall ecosystem.
Multiple implementations of Solid servers are available along with some free public accessible services. We have opted to use the Enterprise Solid Server (ESS) service from Inrupt, Inc., as we did not need to manipulate the server functions. Furthermore, the platform offers a distinct feature of Data Sovereignty, which cannot be found elsewhere. In addition, Inrupt offers client SDKs that simplify the operation of ESS functions:
We have chosen TypeScript and JavaScript as our primary languages because they are the most widely used programming languages in modern web applications. Our implementation utilises the Next.js React framework by Vercel, and we have chosen Ant Design to create the graphical user interface due to its capabilities in speeding up web application development.
The following text will not explain the functions abstracted by the libraries mentioned above.
5.3. Applications
The applications can be categorised into two groups, as described in Concept. The first group consists of applications that are completely trusted, meaning they have unrestricted access to all user data. This includes the ESS services and the citizen application. The second group comprises untrusted applications that have limited access to resources, only when absolutely necessary. This distinction is required because there are also two separate use cases for these applications. In order to establish true ownership of their data, it is necessary that users have access to a fully trusted application which enables them to maintain all of their data without restrictions. Such a Solid app with the ability to view and alter any user data is only achieved by providing unrestricted access. In government applications, unrestricted access should not be necessary as they only consume the provided data when necessary, while complying with [REQ-1] and [REQ-6]. As a result, these two groups are essential to fulfil all aspects of user data sovereignty.
The following table offers a symbolic name and crucial information of implemented applications, including their names, brief descriptions, designated actions and links to public instances. The number of applications was chosen to simulate the complex processes often present in official public service contexts. This approach avoids oversimplification of processes and interconnected dependencies, and creates a realistic and diffuse network of applications.
| Symbol | Name | Description | Tasks | URL |
|---|---|---|---|---|
🐵 |
car-insurance-company |
A car insurer is a company that provides insurance cover for motor vehicles and their drivers against various risks. |
The car insurer offers different types of insurance policies, including liability insurance, comprehensive insurance and additional options such as accident or cover letter insurance. |
|
🐶 |
citizen |
The citizen application provides users with direct access to their maindata and functionality to handle inbox messages. |
||
🦊 |
construction-office |
The construction office is a municipal authority responsible for the planning, approval and supervision of construction projects, as well as for compliance with building regulations and urban development plans. |
Building owners and architects submit building applications to the construction office, which contain detailed information about the planned construction project. The building office checks these applications for compliance with building regulations and issues the necessary permits. |
|
🐱 |
customs |
Customs in Germany is a governmental authority responsible for controlling and monitoring the cross-border movement of goods, collecting customs duties and other charges, and combating illegal activities such as smuggling, money laundering and violations of foreign trade law. |
Customs controls the movement of goods at borders and customs offices. It checks the imported or exported goods to ensure that all necessary documents are present and that the required duties are paid. |
|
🦁 |
employment-office |
The employment office is a public institution in Germany responsible for job placement, employment promotion, unemployment insurance and support for jobseekers and employers. |
The employment office offers support for jobseekers to improve their professional skills and qualifications by promoting further training and qualification measures. |
|
🐯 |
environmental-office |
The environmental office is a state or local authority responsible for the protection and preservation of the environment and the enforcement of environmental laws and regulations. |
The environmental office can issue permits for environmentally relevant activities such as industry, waste disposal, water use and construction projects. These permits are often subject to certain environmental conditions. |
|
🐮 |
land-registry-office |
The land registry office is an authority or institution responsible for the maintenance and administration of geographical information, property data and real estate cadastres. |
The land registry office provides geographical information and geodata for various purposes, including urban planning, land use planning, surveying and research. |
|
🐷 |
parental-benefits-office |
The parental benefits office is an authority or department established in many countries to administer the application, calculation and payment of parental benefits. Parental allowance is a government benefit given to parents after the birth of a child to support them financially when they take parental leave to care for their newborn child. |
The parental benefits office informs the parents how much parental benefit has been granted and for how long. |
|
🐭 |
reconstruction-loan-corporation |
The reconstruction loan corporation is a state development bank in Germany that performs a variety of tasks in the field of financing projects and programmes for economic and social development. |
The reconstruction loan corporation provides financial support to businesses of all sizes to promote investment, innovation and exports. |
https://showcase-solid-reconstruction-loan-corporation.vercel.app/ |
🐹 |
registration-office |
The residents' registration office, is an authority at the municipal level responsible for the collection and management of citizen’s personal data. |
The tasks of the residents' registration office include a variety of services related to residence, identity and personal data. |
|
🐰 |
tax-office |
The tax office is a governmental authority responsible for administering taxes and other financial matters in many countries. |
Citizens, businesses and other taxpayers are often required to file annual tax returns disclosing their income, expenses and other tax-related information. The tax office checks these declarations and calculates the corresponding tax amounts. |
|
🐻 |
trade-office |
The trade office is a municipal-level authority in Germany responsible for regulating and managing commercial activities. |
As a rule, persons who wish to operate a trade must register it with the trade office. The registration serves to officially record the trade activity and to ensure that all legal requirements are met. |
|
🐨 |
vehicle-registration-office |
The vehicle registration office is a state authority responsible for the registration of motor vehicles and related road traffic matters. |
The authority issues vehicle registration plates, which must be attached to the vehicles in order to clearly identify them in road traffic. |
https://showcase-solid-vehicle-registration-office.vercel.app/ |
5.4. Data Modelling
As outlined in the applications section, the applications and services implemented can be categorised into trust groups. This section will provide a thorough examination of this classification. Firstly, we will examine data ownership in detail, followed by a discussion of data creation. This discussion aims to provide an objective and clear overview of the trust groups and their functionality. Additionally, we will delve into authorisations and provide a detailed description of the inputs and outputs of respective applications.
5.4.1. Owners of Data
Citizens are responsible for owning and managing their own data in maindata.ttl.
This resource includes fundamental information that is required for most bureaucratic purposes, including first and last names, as well as place of residence.
In addition, it contains identifiers that are crucial in specific contexts, such as the tax reference number for the tax office.
To reference the relevant previous submission and issuer, data from prior taxes are stored in the dataset.
Offices hold information on citizens from previous submissions or self-collected data. Citizens are granted access to this data related to themselves to ensure transparency and reusability.
5.4.2. Creators of Data
The created data is primarily sourced from citizens themselves, who input it either through the citizen portal or at the relevant office. Any changes require a new submission, similar to existing official processes. However, it is permissible to access and transmit the information, thus fulfilling the concept of the data trustee.
Certain pieces of information comprise data collected or created by the authorities, including land registry data or the tax number. These data may be provided to the user, but cannot be altered by them.
5.4.3. Custom gov RDF Vocabulary
To facilitate all data created by the applications, a custom gov RDF vocabulary has been created to define the necessary predicates.
The following table presents all data references generated by the various applications.
To enhance readability, the predicates are formatted with a namespace prefix.
To generate the complete predicate identifier by expansion, gov:{predicate} would be replaced by urn:gov#{predicate}.
| Predicates | Label | Description |
|---|---|---|
gov:VehicleInsurance |
Motor Vehicle Insurance Certificate |
A document proving that a motor vehicle is insured, providing coverage details. |
gov:BuildingPermit |
Building Permit |
Official authorization from local authorities to commence construction or renovation on a property. |
gov:VehicleRegistration |
Vehicle Registration Certificate |
A document confirming a vehicle’s registration with relevant authorities, containing key details. |
gov:FundingNotice |
Funding Notice |
A document informing recipients about the availability of financial support or funding opportunities. |
gov:BusinessPremisesPermit |
Business Premises Permit |
Official permission allowing a business to operate from a specific location. |
gov:PropertyData |
Property Data |
Information and details related to a specific property, such as ownership, dimensions, and valuation. |
gov:ParentalBenefitNotice |
Parental Benefit Notice |
A document informing parents about their eligibility for parental benefits and the associated details. |
gov:CreditNotice |
Credit Notice |
A document informing an individual or business about a credit-related event or change in credit terms. |
gov:IdentityCard |
Identity Card |
A government-issued document used to confirm an individual’s identity, often including a photograph and personal information. |
gov:TaxDeclaration |
Tax Declaration |
A formal statement disclosing an individual’s or business’s financial details and income for tax assessment. |
gov:TradeLicence |
Trade Licence |
Official authorization permitting an individual or business to engage in a specific trade or occupation. |
gov:LicensePlate |
License Plate |
A plate displaying a unique combination of numbers and letters to identify a motor vehicle. |
5.4.4. Inputs and Outputs of the Applications
The table below displays the predicates and data inputs required for each application. The symbols within table columns are explained in Applications.
In addition to the custom gov predicates, three new standardised predicates from the vcard RDF vocabulary are used.
These are also formatted with a namespace prefix, and by expanding, the prefix vcard:{predicate} would be replaced by http://www.w3.org/2006/vcard/ns#{predicate}.
The table cells indicate whether the combination of application and predicate acts as an input (in) or an output (out).
Optional inputs are marked with a question mark at the end (?).
| Predicates | 🐵 | 🦊 | 🐱 | 🦁 | 🐯 | 🐮 | 🐷 | 🐭 | 🐹 | 🐰 | 🐻 | 🐨 |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
vcard:given-name |
in |
in |
in |
in |
in |
in |
in |
in |
in |
in |
in |
in |
vcard:family-name |
in |
in |
in |
in |
in |
in |
in |
in |
in |
in |
in |
in |
vcard:locality |
in |
in |
in |
in |
in |
in |
||||||
gov:VehicleInsurance |
out |
in? |
||||||||||
gov:BuildingPermit |
out |
in |
in |
|||||||||
gov:VehicleRegistration |
out |
in |
||||||||||
gov:FundingNotice |
out |
|||||||||||
gov:BusinessPremisesPermit |
out |
in? |
in |
|||||||||
gov:PropertyData |
in |
in? |
in |
out |
in |
in |
||||||
gov:ParentalBenefitNotice |
out |
in? |
||||||||||
gov:CreditNotice |
out |
in? |
in? |
|||||||||
gov:IdentityCard |
in |
in |
in |
out |
in |
in |
||||||
gov:TaxDeclaration |
in |
out |
||||||||||
gov:TradeLicence |
in? |
in |
in |
in |
in? |
out |
in? |
|||||
gov:LicensePlate |
out |
The vcard predicates in the table above belong to the citizen’s maindata and are directly accessible to all applications, if authorized by the user.
Whereas all the gov predicates are references to previous submissions to the respective office for use by the citizen.
The actual data of the application is hidden behind the reference.
5.5. Scenarios and Processes
The sequence diagrams below illustrate the processes showcased. One diagram illustrates the complete usage scenario, whereas the remaining diagrams portray the recurrent sequences within it.
To enhance diagram clarity, reference blocks are utilised to represent these recurrent sequences. These referenced subprocesses always include the participants furthest to the left and right, as indicated by their width. Furthermore, some participants in between may also be involved.
For simplicity, the diagrams do not include differentiation between client and server functions, as it bears a limited relevance and would unnecessarily enhance the diagram’s complexity. Communication between the client and server of the same participant is indicated by an arrow pointing from the participant to itself, similar to other actions targeted at itself. In addition, in cases where basic read/write/append operations are performed on data, the following diagrams condense the request and response actions into a single arrow pointing in both directions.
As previously described, offices serve as representatives for the web applications listed in Applications. Office 1 and office 2 are introduced in the following diagrams to clarify the communication process between two representatives. These offices serve as placeholders for relevant participants and do not represent specific offices. Furthermore, the meaning of office 1 and office 2 may vary between the different diagrams.
5.5.1. Overall Architecture
The diagram below shows the entire procedure of utilising the applications. The process assumes the existence of an identity and data storage, which may not possess the necessary file or folder structure and permissions for the process to be carried out.
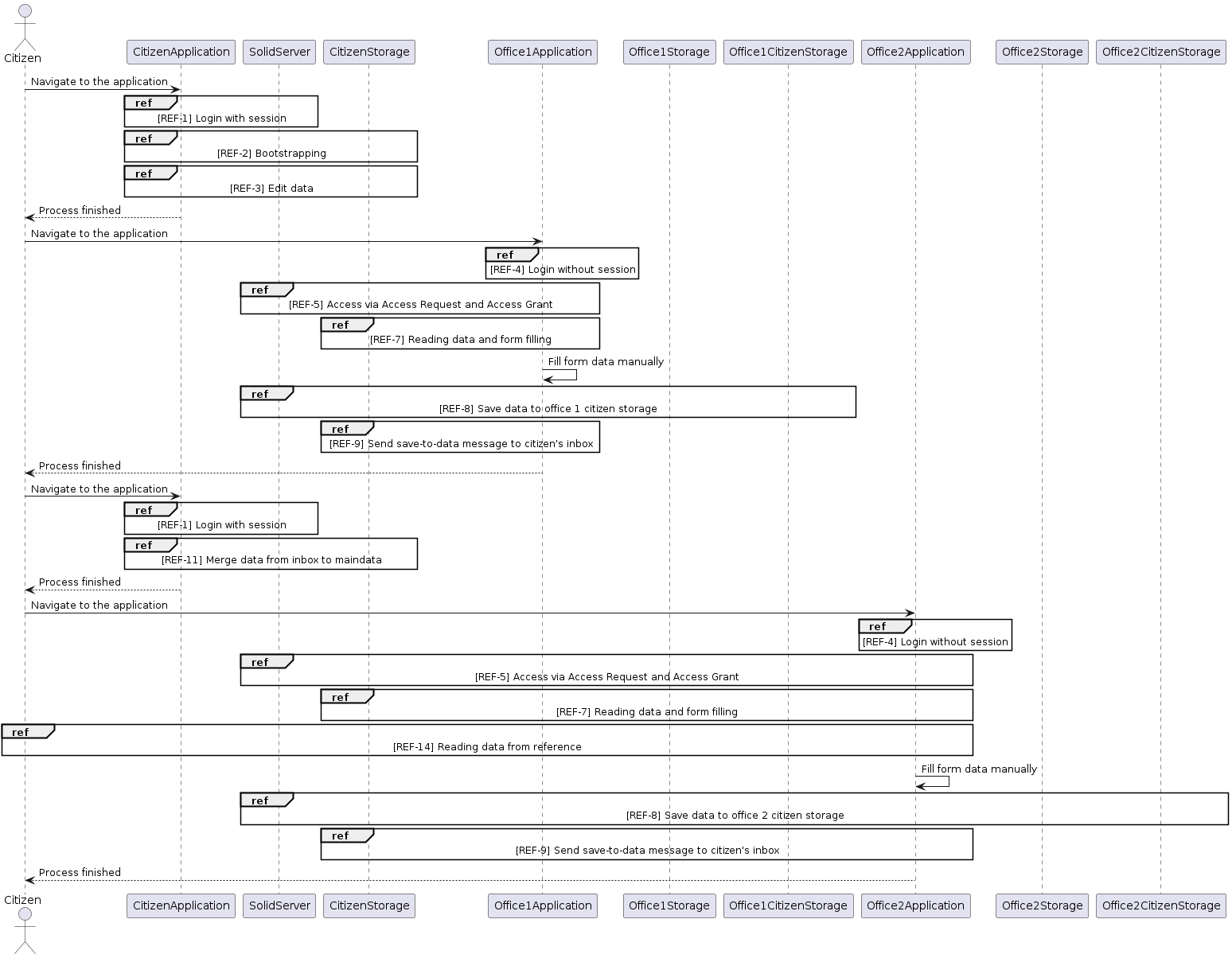
5.5.2. References
The overall sequence diagram uses a variety of repetitive referenced subprocesses, which are detailed here. The diagrams explained are listed in the order of their appearance in the overall diagram.
[REF-1] Login With Session
The login process is defined by Inrupt as described in the software library.
As this mechanism was not manipulated, we omit its sequence diagram. Authentication in the browser was partially facilitated through the Inrupt Solid React SDK, utilising the adapter library for login functions.
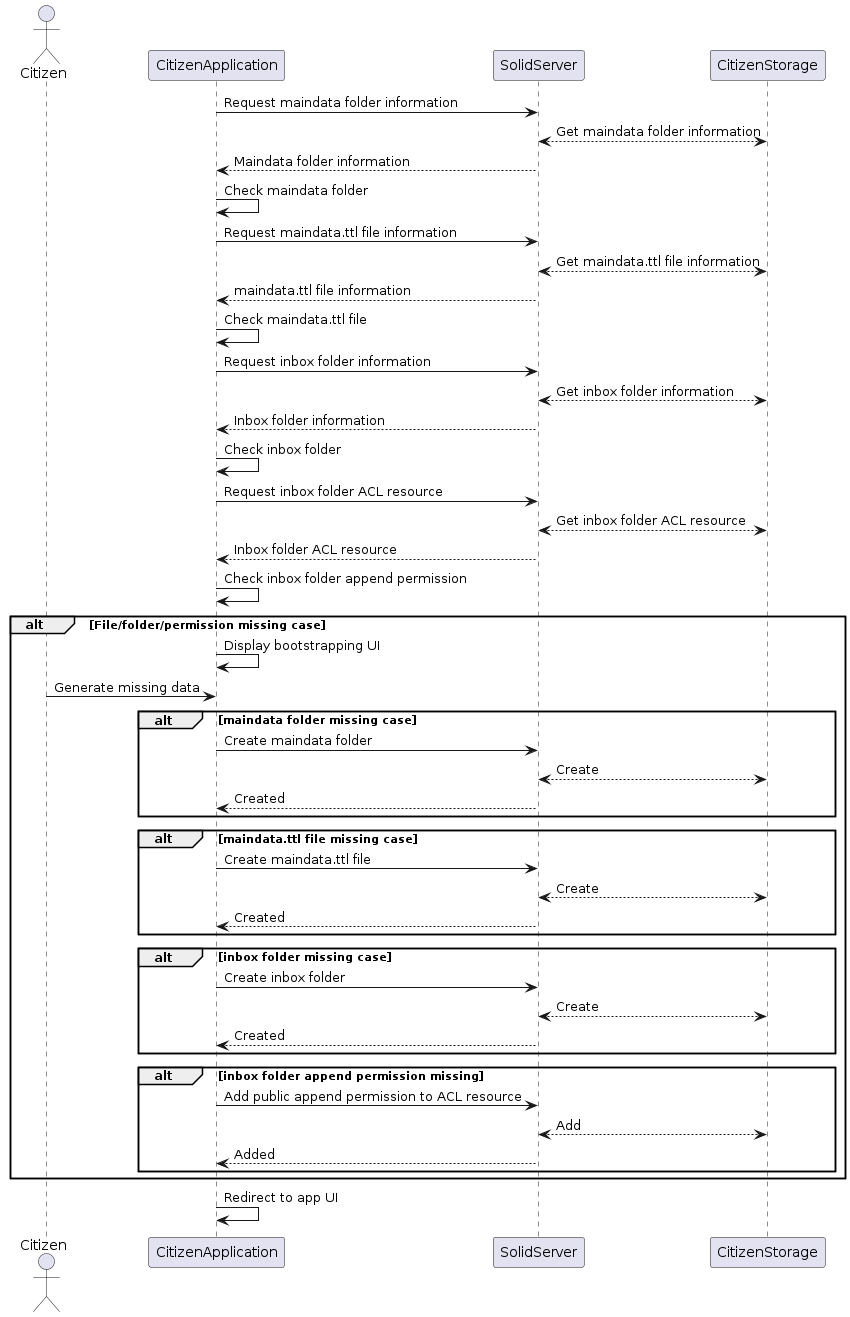
[REF-2] Bootstrapping
The diagram illustrates bootstrapping via the application to establish the essential structure and access rights in the data storage.
[REF-3] Edit Data
Editing the data is a straightforward process and not displayed in a sequence diagram due to its simplicity. The Inrupt JavaScript Client library functions were utilised for reading and writing data to the data storage. For more details on this mechanism, refer to Read/Write Structured Data.
The data was presented through the user interface (UI) library’s form component and transformed through adapter patterns.
[REF-4] Login Without Session
The process of logging in without a session cannot truly be considered a log-in, as it lacks any authentication. Rather, a WebID is produced based on the username and used in subsequent authorisation procedures. This approach guarantees that applications are only granted the bare minimum of permissions and that authorisations must be specifically requested for each resource.
[REF-5] Access via Access Request and Access Grant
The sequence diagram depicts the Access Grant Service as implemented in the ESS. This procedure utilises the ACP specification to selectively release resources to an application. Only after explicit user permission can the resources be accessed.
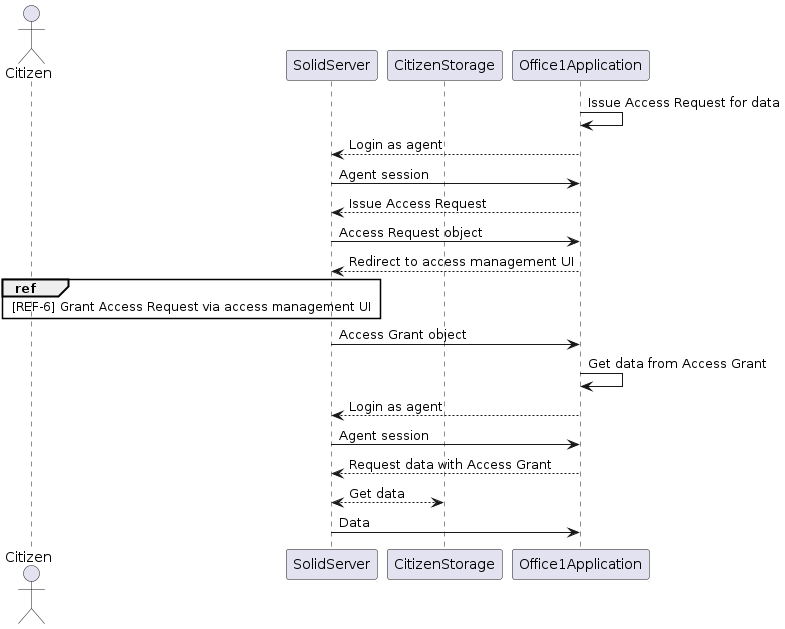
For more details on this mechanism, refer to Access Requests and Grants.
[REF-6] Grant Access Request via Access Management UI
Users can grant or refuse an agent’s Access Request via the provided access management UI of the Inrupt PodSpaces. This involves the user logging in and explicitly choosing access rights for the requested resources as well as optionally specifying the duration of access. ESS will then create an Access Grant with the according status, which allows the agent to access the related resource. This service is used as is, and was not modified for this particular use case.
[REF-7] Reading Data and Form Filling
Reading and completing forms utilises the same process as editing data and can be followed in this section. The only variation is that there is a fixed data model in this procedure, as opposed to the dynamic creation of data when editing.
[REF-8] Save Data to Office n Citizen Storage
As depicted in the illustration below, the data provided by the user is stored in an isolated data storage that exclusively safeguards the data of one user. The primary objective of this measure is to heighten the difficulty of unauthorised access. The WebID affiliated with the application is the creator and owner of the storage and the submitted data. The concept of a data trustee is incorporated by issuing the submission’s reference via read access.
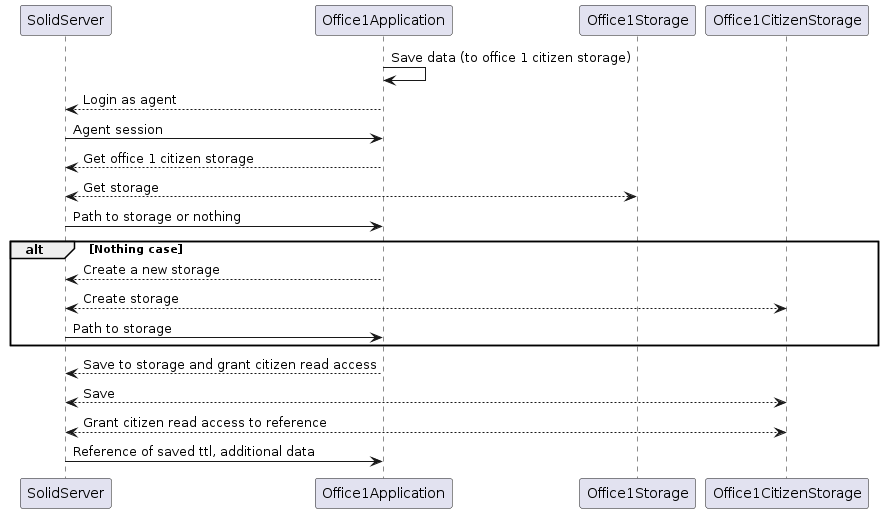
n citizen storage. Source: own figure[REF-9] Send save-to-data Message to Citizen’s Inbox
As outlined in the [REF-4] Login Without Session documentation, government applications lack true authentication measures. This raises the question of what steps are required for processing user data. Therefore, an inbox mechanism is employed to attach a Turtle file to the user’s publicly accessible inbox directory for subsequent processing in an application with enhanced privileges.
This sequence illustrates the use case of creating a save-to-data message and saving it to the user’s inbox.
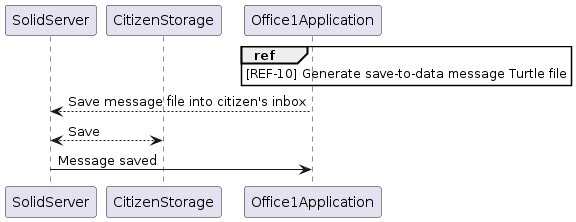
[REF-10] Generate save-to-data Message Turtle File
The generation of message data only involves simple Turtle text creation from supplied data. Consequently, there is no need for any sequence diagram to further illustrate this process. As a significant part of this type of message generation, the identification as a save-to-data message is stored in the message Turtle data.
[REF-11] Merge Data From Inbox to Maindata
To process save-to-data inbox messages, the message body is merged with the maindata.ttl file, and any existing data is overwritten as required.
This is a straightforward operation that is not depicted graphically here.
[REF-12] Send Request Access Message to Citizen’s Inbox
This sequence illustrates the use case of creating a request access message and saving it to the user’s inbox. The process follows the same steps as shown in [REF-9] Send save-to-data Message to Citizen’s Inbox and differs only in the content of the generated message.
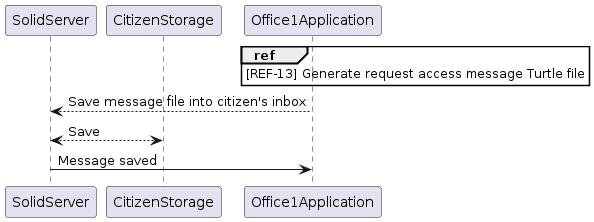
[REF-13] Generate Request Access Message Turtle File
For the same reasons as given in [REF-10] Generate save-to-data Message Turtle File, no graphical representation of the process is necessary. In this message generation type, the identification as a request for access message is stored in the message Turtle data.
[REF-14] Reading Data From Reference
The process of reading reference data is composed of two distinct sections, as presented in the diagram below. The first stage includes the access to the referenced data. If the application is not yet authorised to access the data, an additional subprocess is initiated to request the necessary permissions. In the second stage, the user has the option of granting or denying the Access Request via their inbox. This custom functionality is necessary because the ESS Access Grant services do not provide a way to grant access to a resource to another participant if the user is not the actual owner of the data or does not have full access.
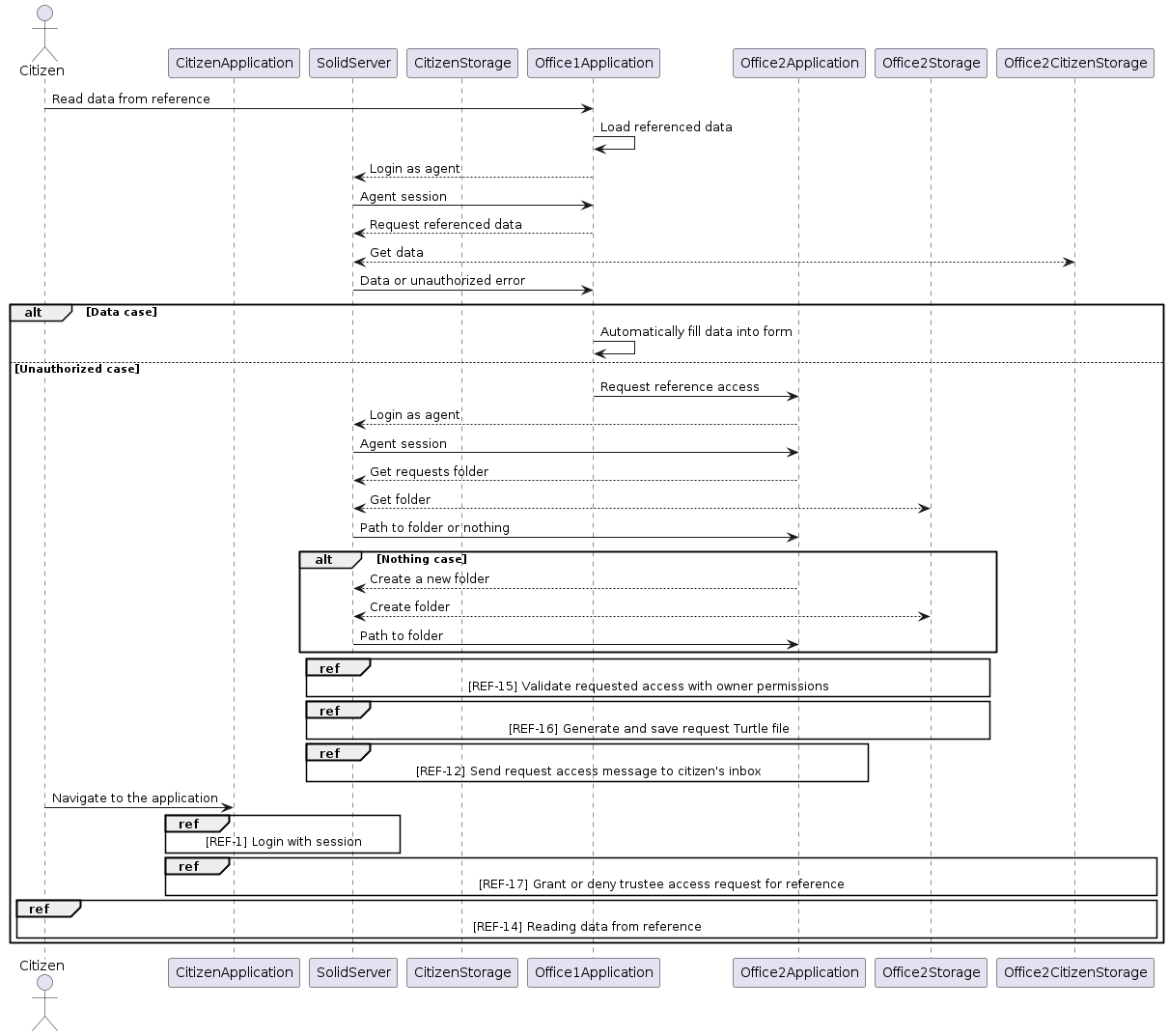
[REF-15] Validate Requested Access With Owner Permissions
Before creating an Access Request, the owner’s permissions must first be used to validate the requested access. This process ensures that the owner possesses all the requested access permissions, thereby allowing them to grant these permissions to other participants.
[REF-16] Generate and Save Request Turtle File
This process consists of generating a basic Turtle file containing the request information, followed by storing the generated file in the office storage. At file generation, an initial pending status is added to the Turtle data to allow the request status to be checked and updated in subsequent processes.
[REF-17] Grant or Deny Trustee Access Request for Reference
The sequence diagram visualises the user-initiated process of granting or denying a request for access to a referenced resource as the data trustee. If access is granted, all the requested permissions are provided to the original requester. If access is denied, no further changes to permissions are required, as the requester does not possess any initial access permissions. In either scenario, the request state is updated based on the user’s decision to avoid multiple uses of the request.
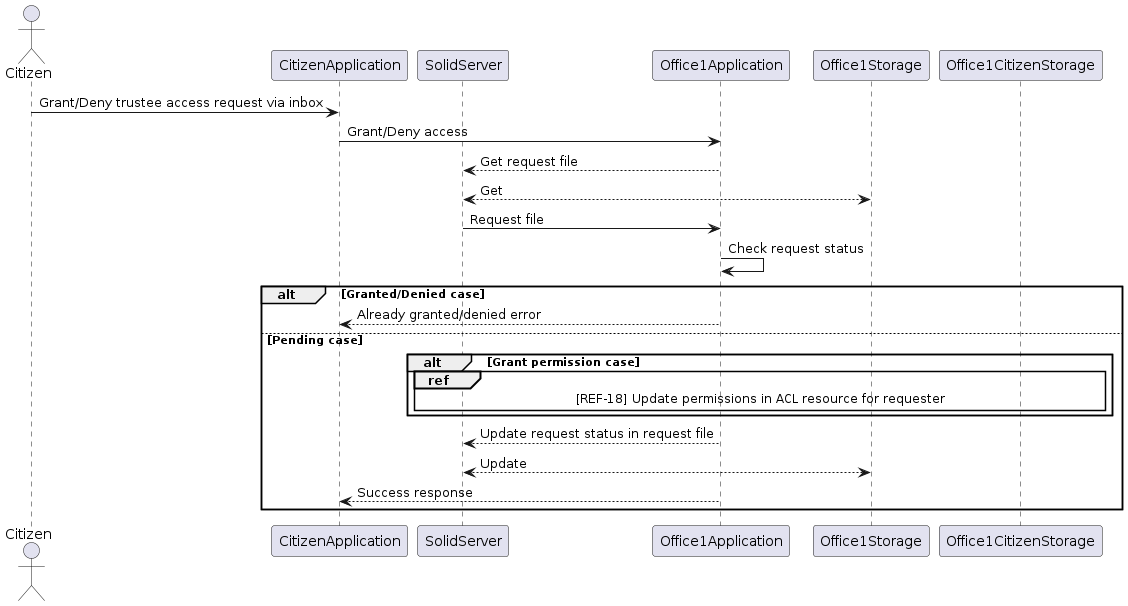
[REF-18] Update Permissions in ACL resource for Requester
This process uses ACL resource functionality based on the ACP language to grant requested access permissions to resources. This involves adding the requester and requested permissions to resource-specific ACL resources and updating them in the data storage.
5.6. Implementation Strategies
This section covers various implementation strategies and approaches that were relevant during the project. It outlines specific development choices and describes customised solutions for required features. The section also outlines failed attempts, providing context for the final successful solutions and why these were necessary over more straightforward options.
5.6.1. Access Granting and Policies
The widely supported ACL resource functionality provides simple ways to manage resource access for different users. It allows read, write, append and control permissions on resources enabling control of user and application access to data, by providing an associated ACL resource for each resource in a storage instance. However, this mechanism has several limitations. These include the lack of timed access permissions and the lack of partial control permissions for other users. Additionally, the Solid providers do not offer a straightforward method for users to manage access permissions defined in the ACL resource, through a management UI.
The alternative permission mechanism of Access Requests and Access Grants aims to address several of these issues. It allows permissions to be granted on a timed basis to prevent unlimited access and provides a simple access management UI to handle Access Requests. The main drawback of this approach is its current Solid server support, as only the Enterprise Solid Server provides an implementation. Additionally, it only functions when the user granting access also owns the data.
Since both approaches to access management have different advantages and disadvantages, it was necessary to make use of both depending on the use case.
Our citizen application requires complete access to the user’s data storage. It must be able to read and create folders, files, and permissions as detailed in [REF-2] Bootstrapping. Implementing this functionality through Access Requests and Access Grants is impossible or would result in confusing behaviour due to multiple Access Requests for various resources. Therefore, this application relies on ACL resources as the access management feature and assumes that the user has full access to the data storage, which is implied as the user is the storage owner. This approach enables the citizen application to function as a trustworthy management tool for accessing user data, following a complete session login, as depicted in the initial steps of the Overall Architecture.
Our government applications cannot be treated as trusted management tools with complete access to the user’s data storage. Only the necessary data should be requested when required, according to [REQ-6]. These constraints are incompatible with the ACL resource approach, as a full session login would be necessary, granting full access to all data. Therefore, these applications rely on Access Requests and Access Grants to request only the required data when it becomes necessary, as described in the second part of the Overall Architecture. This dependence on Access Requests and Access Grants required utilising the official Enterprise Solid Server implementation provided by Inrupt. However, this is not a significant drawback, as all other server implementations are still progressing in the adoption of Solid standards and will support comparable mechanisms in the future.
5.6.2. UI/UX
One of the challenges in this project has been to keep the processes user-friendly (see [REQ-3]), but still adhere to the requirements [REQ-1]/[REQ-5]. Ideally, applications should not have full access to read/write data in the user’s personal data storage unless absolutely necessary. However, to populate a user’s data storage with the necessary maindata files, to be able to use government applications, this could not be realised with Access Grants, since it is not possible to send an Access Request to create a specific (container) resource (e.g. maindata and inbox) without granting write access to the entire data storage. In order to keep the UI easy to use and self-explanatory, we opted to not require users to edit raw RDF files and instead focused on designing data flows for specific purposes.
5.6.3. Additional Mechanisms
A few of the mechanisms we have found to be necessary for our showcase were not provided by the Solid specification itself or the used Solid provider. In these cases, it was necessary to create custom mechanisms to implement the required functionality.
Application Data Storage Specific to a User
The Solid specification was built with the intention of users maintaining all their data in their own personal data storage.
In this showcase, one of the requirements ([REQ-5]) is that users cannot further modify an official form after submitting it at a government office.
At the same time, they need to be able to access any submitted data and, if necessary, grant access to other applications.
This combination of access permissions cannot be achieved in a user-owned data storage, as the user is always automatically granted all possible permissions.
As a solution to this issue, a different participant must be the owner of the data storage and explicitly grant only the necessary read permissions to the user.
For these reasons, government applications in this showcase create multiple data storages, each specific to a WebID, but owned by the government application.
This makes it possible for users to access data they have submitted at an office, without being able to change the submitted data.
See [REF-8] Save Data to Office n Citizen Storage for a detailed diagram of this mechanism.
Granting Access to Other Participants
Granting access to data outside the user’s data storage is not included in the Solid specification, as it is designed to allow users to maintain only their own data. In our particular case, the user is not the owner of all the available data. However, they still need to be able to grant read access to other applications. Several approaches were explored to satisfy these requirements.
Initially, the Access Grant Service implemented in the ESS was utilised, as it already served as a mechanism for other applications to access data stored in the user’s data storage. However, this method proved problematic, as Access Requests are always directed to the owner of the requested data. In this scenario, the owner is not the user who should grant access. Instead, a separate government application controls the data. Therefore, only the original government application would be able to grant access, not the user. As a result, this approach did not offer the functionality necessary to access data controlled by another participant.
In the second approach, a modification of the process outlined in [REF-8] Save Data to Office n Citizen Storage was implemented to grant the user control write access beforehand by modifying the ACL resource associated with the resource of which the user is a trustee, thus enabling them to manipulate the permissions set for the connected resource.
This allowed the user to grant read access to any third party application, allowing them to access the data stored in another application’s user storage.
However, the user gained full editing rights to the resource permissions through control write permission.
This enabled them to grant write access to other participants, including themselves, even if they only had read access.
This loophole rendered the approach unfeasible, as the user could edit data uploaded to a government application, which is not permitted according to [REQ-5].
The final approach uses a fully custom-built mechanism to create and process data trustee access requests. All applications provide a custom server functionality that allows users to extend their access permissions to other participants for data stored in the application’s user storage. This includes the creation of custom request files, their storage in the application storage and the ability for users to grant or deny them via another custom server functionality. Resource permission modifications via ACL resource are carried out by the government application that owns the resource. All requested permissions are compared to the user’s access rights to prevent problems encountered when directly modifying permissions in the ACL resource as a user, as seen in the second approach. A detailed description of this process is provided in [REF-14] Reading Data From Reference.
Inbox With Write-Back and Access Granting Mechanism
To ensure that individuals are made aware of changes occurring in their respective government data storages or applications that request access to data, a messaging service is required. The Solid specification includes a Notification Protocol. The ESS services implement this protocol as WebSocket notifications, as specified in the Solid Notifications Protocol. Further information about the current implementation in the ESS can be found at Subscribe to WebSocket Notifications. This system provides real-time updates on known and owned data, but no means of creating and storing messages for later processing. Additionally, in our scenario, the user is not the owner of all resources and folders that require notifications.
Due to these reasons, it was necessary to create a customised messaging mechanism to provide the user with the necessary tools. In order for this feature to work correctly, it is necessary to create an inbox folder in the user’s main storage that has public append access enabled. This step is ensured by the mandatory bootstrapping procedure detailed in [REF-2] Bootstrapping. This folder is used by other applications to store messages as Turtle files in the user’s storage. Through the citizen app, users can view and handle these incoming messages.
For our showcase, two message variants with custom inbox functionality were required: a save-to-data message and a request access message. The save-to-data message ([REF-9] Send save-to-data Message to Citizen’s Inbox) allows the user to transfer incoming data from other applications back to their maindata, see [REF-11] Merge Data From Inbox to Maindata for more information. The request access message ([REF-12] Send Request Access Message to Citizen’s Inbox) enables the user to grant the requested permissions to other applications, as previously outlined in [REF-17] Grant or Deny Trustee Access Request for Reference. By implementing these two message types, we were able to provide essential additional functionality that was not originally incorporated in the Solid specification.
6. Discussion
In this chapter, we will discuss some of the challenges encountered while working on the e-government showcase under Solid specifications. The development of this showcase touched on many different topics, such as the use of specifications and libraries, designing data flows and keeping access control in the hands of the user, while also making the UI easy to work with and accessible. For nearly every step, a different approach could be considered, and a lot of starting points for further research can be found.
6.1. Conceptual Realisation
As outlined in Concept, we designed two different types of applications; multiple government applications representing public administration offices, as well as one citizen application, used to manage personal data. In order to reduce effort required by citizens to effectively navigate bureaucratic processes, one of the important requirements was the interoperability of all applications Interoperability is also an integral part of the Solid specifications, and we found the general architecture consisting of data storages, agents and applications to be well-fitting for the purpose of public administration services. We observed that building multiple applications with logically linked data requirements based on the same concepts can help reduce the effort needed to develop each individual application. Providing applications with a similar structure and design can also improve upon the usability and accessibility of public services, since a familiarity with structures and interfaces could help citizens navigate the processes more easily. Although gaining a deep understanding about data processes in public administration services on an operational level was not feasible in the scope of this work, the general assumption can be made that with further specification of data and processes required by different public administration offices, the ideas developed could be improved upon and expanded. However, it is important to note that all applications and processes developed in this work rely upon a limited understanding of the domain of public administration service processes and regulations. Certain aspects, e.g. legal restrictions could not be included in designing the scenarios.
Other additions to specific technologies may be required in further development, and need to be evaluated separately. Many technologies and applications specific to public administration services in Germany are already established or under development. These need to integrate with e-government application under Solid specifications. One aspect where this might be needed is providing other identification services in combination with the Solid WebID Profile. Available technologies in Germany are e.g. the electronic identity card or the BundID.
6.2. Data Sovereignty
Giving the users full control of their personal data and providing transparent data flows as well as facilitating access to already submitted or produced data is one of the most important aspects of the specified scenario. Since the Solid specifications aim to give a reference for those standards, many of the included technologies integrated well with the planned architecture. Controlling data access with the ACL resources can serve as an entry point for those concerns. We have found the specifications lacking in the context of usability, as manually setting access rights for specific resources requires the user to be familiar with the general concepts of data storage and Solid servers, as well as understanding the fundamental access modes in the ACL resource.
There are two main concerns in our implementation regarding this:
Firstly, we decided to further limit the scope of our implementation to work with the Access Grant Service implemented by the Solid Enterprise Server (ESS). The service allows applications to directly request access to any resource, specifying which access modes are needed and optionally a time frame for which the access is granted. Other server implementations don’t yet support this feature, and this project was limited to creating Solid applications, while using a reference implementation of a Solid server. Some functionalities of the government office apps, like initialising data storages for each citizen, might have been more straightforward implementation-wise if we had built a dedicated Solid server. Our decision to focus on the ESS implementation has made it possible to make use of the Access Granting mechanism, but because of that, the applications built in this showcase are not compatible with other Solid providers. While it is likely that other providers will have a similar feature in the future, as the concept is featured in the Solid access control policy specifications, it is a drawback that the applications developed in this showcase are not independent of the user’s choice of Provider.
The second important subject concerning data sovereignty is the data access in the citizen app. Applications in this showcase require specific resources being present in a data storage, such as the maindata and inbox. The citizen application developed in this showcase requires read and write access to a data storage in order to create these resources with a bootstrapping mechanism, as described in the chapter implementation [REF-2] Bootstrapping. Users might be hesitant to use their personal data storage with official government applications, if it contains data from other sources or applications. While Applications that provide users with the tools to edit all their data freely by themselves by design need full access to a data storage, solutions could be found to provide users with a way to create these necessary resources with any other Solid application they prefer. One way to achieve this could be providing description resources (e.g. using the Protocol for Web Description Resources [27]) for the needed (container) resources, which Solid applications could use to initialise a users Solid storage according to the description provided. While the use of description resources is featured in the Solid protocol under section 4.3 Auxiliary Resources, there is not yet a specification for initialising storage resources based on description resources.
6.3. Citizens as resource trustees
We have found that since the Solid specifications were developed with Social Web Applications as a background, where all resources concerning an agent are typically owned by that agent themselves, some of the necessary structures and mechanisms needed to mirror the processes of public administration services had no equivalent model in the specification.
One of those features is the ability to grant access to resources of which a user is not the owner, but the trustee. This distinction is important since resources produced by government applications on behalf of an individual need to be owned by those offices to ensure consistency and offer a single point of truth. In the implementation, we conceptualised this by creating a separate storage for each citizen using a government application, to which they will be granted read access, based on their WebID. Since many public administration processes require citizens to forward data produced by one public entity on their behalf to another, citizens need to be able to provide read access to those resources to other agents.
As described previously in section Additional Mechanisms, in this implementation different approaches were tested and evaluated against the specified Requirements.
The implementation proposed in this work features a functional mechanism for government applications to request access to a resource owned by another government application, which will be granted after confirmation by the trustee. However, it should be noted that this feature should only serve as a reference as it is experimental and further specifications would be needed to ensure security in this process.
6.4. Working With the Solid Framework
We have found that one challenge in working with the developing specifications and frameworks was the difficulty in planning and developing an application based on standards and libraries that are in different stages of development. One of the biggest issues is the lack of standardised patterns in the libraries. This has been pointed out by developers and designers interviewed at SolidLab Flanders [23] as well, with developers mentioning a lack of design patterns as the second-biggest challenge in developing Solid applications. The patterns mentioned most in that survey are login and consent flow. Given that the libraries and reference implementations are still in development, some standardisation could be an important next step. There are two main issues that could be solved by standardised implementations: Firstly, additional standardised patterns make it easier to develop Solid applications, which could lead to more people adopting the standard, and secondly, recognisable patterns make the applications easier to understand and use.
Differences in terminology between the JavaScript libraries and SDK, the Enterprise Solid Server documentation and the Solid specification itself made development more difficult and can be seen as severe risks in the development of applications, especially if it concerns security and authorisation features. The initial design of features or processes, based on the Solid specification, needed to be adapted throughout development as the provided library implementations diverge from the specification or not yet realise all needed features. This resulted in reduced quality as several different approaches had to be developed, often containing workarounds for these limitations. As such, some of the developed solutions are highly experimental, which is a direct consequence of problems encountered with the current state of the Solid specification and framework. Some of these workaround implementations and failed approaches are further detailed in Implementation Strategies.
6.5. UI/UX
In order for e-government applications to be accessible, an intuitive User Interface is an important requirement. We specified this previously as "Applications should not require deep understanding of underlying technologies on the user side […]" [REQ-3]. Since advanced end-user testing hasn’t been in the scope of this work, the following insights are based on qualitative observations and feedback.
One of the primary challenges encountered in implementing the User Interface within the Solid framework relates to data flows. Several aspects were found to be confusing for users. Users may encounter difficulties understanding how data moves within the system, potentially leading to frustration or mismanagement of personal data. Similarly, the login and authentication flow might not be easily understandable for users, especially distinguishing between signing in using a session and merely providing a WebID without signing in. This differentiation may not be immediately clear to users and can create uncertainty about their status within the system. Access rights management is a critical element of all applications developed in this work, and likewise is not something most people use regularly. Particularly, since access granting works differently for citizens' personal data storages and those owned by government offices on behalf of the citizen. Users may find the multitude of steps involved in granting access to be overwhelming and time-consuming.
In addition to these challenges, a substantial factor in the implementation and adaptation process revolves around understanding the Solid specifications and navigating the associated terminology. Our experience aligns with the findings in the previously mentioned series of interviews conducted by SolidLab Flanders [23], which identified the challenge of making Solid concepts explainable as a top concern for Solid app developers. Users need accessible explanations and intuitive interfaces to engage effectively with Solid-based applications. In future work on these or similar applications, these concerns should be emphasised.
6.6. Data Models
In order to apply the Solid specifications to the use case, all resources need to be provided as RDF triples and as such stored as Turtle files. As such, all resources in a Solid storage are processable by a vast number of applications, since it is a non-proprietary standard and most RDF resources are described using shared ontologies and vocabularies specific to and across various domains. This makes shared and collaborative management of knowledge and data possible. In approaching this project, we were confronted with the challenge that public administration processes and entities are one domain, that does not yet have an agreed upon vocabulary for Linked Data.
The Chapter Data Modelling focuses on the implementation aspects concerned with modelling
data required in the administration processes as RDF resources.
Since in this project the focus was on developing applications, that closely mirror existing processes,
we decided to create a custom vocabulary for specific data types( see also [Custom gov RDF Vocabulary]).
Alternatively, existing Vocabularies could be used,
such as the Vocabulary of Interlinked Datasets.
We have found that even with the reduced complexity of the government applications and data flows designed in this showcase,
compared with those needed for more complex bureaucratic processes,
no already established vocabulary features needed predicates, such as tax reference number or trade licence.
Creating a vocabulary of predicates not only facilitates automated processing of information, but can also serve as a tool for information discovery and sharing. As such, creating a vocabulary for representing data relevant to e-government processes could be both a tool to provide insights into the connections between data types and processes as well as serve as specification for the design of applications in this domain.
The showcase developed in this work can serve as a reference implementation for utilising existing Linked Data principles, and more specifically, the Solid specifications to design e-government applications. However, in order to effectively and securely build on this, a common vocabulary for sharing personal data related to public administration services is needed.
6.7. Conclusion
This work aimed to develop a showcase for e-government services as Solid applications. We proposed an architecture of logically linked applications that utilises Linked Data principles in order to facilitate sharing personal data with different public entities. This features a citizen application, used to manage a citizen’s personal data storage, which is accessed via a Solid server, as well as government applications, that facilitate sharing data with different public offices. All government applications require different information from citizens, which is entered on a UI form. They then provide a service, which can be storing entered data as official documents or additionally providing certain personal data to the citizen, which can be saved in their own storage.
We found that the Solid specifications were generally well applicable to this context. Established standards and implementations were used to ensure data sovereignty, such as managing access via Access Requests and Grants. However, some specific custom workflows needed to be implemented, mainly concerning the storing of citizen data by government applications. We proposed a model for this, where government applications create a separate storage instance on the Solid server for each citizen, who will then be the trustee of all resources in that storage. Trustees can access and share these resources. This is a scenario not touched upon in the Solid specifications, and as such, no standardised workflow exists. As applications or Solid servers developed in an e-government context will need these functionalities, in order to further develop such services, additional specifications need to be provided.
Additional further challenges, such as designing usable and understandable user interfaces, ensuring data consistency and working with RDF vocabularies have been described in this chapter.
All highlighted shortcomings of preliminary specifications when applied to e-government applications, should not be understood as arguments for deeming the Solid specifications fundamentally flawed or inapplicable in this scenario. Rather, they should be seen as a basis for future research.
7. Summary
In this project, we explored the implementation of the Solid project specifications in the context of e-government processes in Germany. The Solid specifications offer a framework for securely storing data in decentralised data storages, with granular control over data access. We discussed which specifications within the solid framework can be used to create secure web applications for e-governance and identified certain limitations or areas where these specifications may fall short.
These are the key findings and takeaways from this showcase:
We found the Solid specifications generally applicable to e-government processes. Particularly, the emphasis on interoperability based on the Solid model, involving providers and applications, has shown promise in working seamlessly with various government applications, enabling users to share personal data with different public administration offices.
According to our experience, current technologies, including libraries and reference implementations of providers, are not yet mature enough to streamline development for wider adoption. However, certain Solid specifications and technologies, such as creating a WebID and initialising data storages, have proven to be valuable assets in this showcase and work reliably within the framework.
The Solid specifications propose a wide array of technologies and methods for giving users control over their data and which agents can access which resources.
We have found the specifications to be lacking for some use-cases in this particular showcase, i.e. data flows, where a citizen is not the owner, but the trustee of a resource. The absence of features for managing data on behalf of citizens by public administration offices has made some derivations from standard solid workflows necessary. Our proposed authorisation flows for these cases are a working example, but for more secure development, a standardised specification for those scenarios is necessary.
The previously mentioned granular control over access and permissions only applies to generic resources, such as folders or files. Presently, the Solid specification does not provide any means to regulate access to specific data entries within resources. The only way to enable such functionality is through supplementary procedures, like providing a separate authorising trustee. Further research could explore easy and secure methods to directly allow this functionality.
Nevertheless, the Solid specifications can serve as a valuable reference point for designing interoperable e-governance applications. Further research and development should be encouraged, since working within an already established framework of technologies can facilitate the development of new applications. It should be especially noted that the Solid framework is not a commercial product, but an open-source project and as such dependent on research and insights from the community. Seeing as there have been multiple research and development projects applying the Solid specifications to various use-cases, the findings in this work should be re-evaluated in the future.
Since the showcase focuses on applications in the Solid framework and only works with the ESS as a provider, limited insights were gained regarding the broader challenges in developing Solid server technologies. However, there is potential for future development of Solid servers to accommodate the needs identified in this showcase.
Adapting the Solid concept for e-governance poses a significant challenge, especially in making it accessible to users who may not have an in-depth understanding of Solid principles. Further research is required to create user-friendly ways of interacting with Solid applications and data models.
A major obstacle encountered is the lack of an established RDF vocabulary for public administration processes and documents in Germany. While this work didn’t focus on converting existing processes into RDF models, we can say that well-defined ontologies are a major factor in designing solid applications. But even in a broader context, a well-defined vocabulary and terminology is needed in order to create reliable and accessible e-governance applications. In designing this showcase, it became evident that the theoretical foundations, particularly regarding RDF resource modelling, require further interdisciplinary assessment.
In conclusion, this showcase highlights the potential of the Solid project specifications in enhancing e-government processes, with a focus on interoperability and user-controlled data management. While there are challenges to overcome, such as technology readiness and user-friendliness, further research and development in this domain could lead to significant advancements in the field of e-governance. Additionally, specifying an ontology for e-government processes is essential for the successful adoption of Solid in governmental contexts.
References
-
[1] ‘Dashboard Digitale Verwaltung’. Accessed: Sep. 25, 2023. [Online]. Available: https://dashboard.ozg-umsetzung.de/
-
[2] E. Hilgendorf, ‘Datensouveränität | bidt’, bidt DE. Accessed: Sep. 18, 2023. [Online]. Available: https://www.bidt.digital/glossar/datensouveraenitaet/
-
[3] B. Wolford, ‘What is GDPR, the EU’s new data protection law?’, GDPR.eu. Accessed: Sep. 18, 2023. [Online]. Available: https://gdpr.eu/what-is-gdpr/
-
[4] C. Sarven, T. Berners-Lee, R. Verborgh, and K. Kjernsmo, ‘Solid Protocol Introduction’. Accessed: Sep. 29, 2023. [Online]. Available: https://solidproject.org/TR/protocol#introduction
-
[5] C. Sarven, T. Berners-Lee, R. Verborgh, and K. Kjernsmo, ‘Solid Protocol’. Accessed: Sep. 18, 2023. [Online]. Available: https://solidproject.org/TR/protocol
-
[6] ‘RDF 1.1 Concepts and Abstract Syntax’. Accessed: Sep. 29, 2023. [Online]. Available: https://www.w3.org/TR/rdf11-concepts/
-
[7] D. Beckett, T. Berners-Lee, E. Prud’hommeaux, and G. Carothers, ‘RDF 1.1 Turtle’. Accessed: Sep. 18, 2023. [Online]. Available: https://www.w3.org/TR/turtle/
-
[8] A. Sambra, H. Story, and T. Berners-Lee, ‘WebID 1.0’. Accessed: Sep. 20, 2023. [Online]. Available: https://www.w3.org/2005/Incubator/webid/spec/identity/
-
[9] S. Capadisli, ‘Web Access Control’. Accessed: Sep. 20, 2023. [Online]. Available: https://solidproject.org/TR/wac
-
[10] M. Bosquet, ‘Access Control Policy (ACP)’. Accessed: Sep. 20, 2023. [Online]. Available: https://solidproject.org/TR/acp
-
[11] ‘Access Requests and Grants’. Accessed: Sep. 29, 2023. [Online]. Available: https://docs.inrupt.com/ess/latest/security/access-requests-grants/
-
[12] ‘Datentreuhänder’. Accessed: Sep. 30, 2023. [Online]. Available: https://www.bundesdruckerei-gmbh.de/de/loesungen/datentreuhaender
-
[13] ‘Behördengänge online erledigen: E-Government’, Bundesministerium des Innern und für Heimat. Accessed: Sep. 23, 2023. [Online]. Available: https://www.bmi.bund.de/DE/themen/moderne-verwaltung/e-government/e-government-node.html
-
[14] E. Mansour, A. Sambra, S. Hawke, M. Zereba, S. Capadisli, A. Ghanem, A. Aboulnaga, and T. Berners-Lee. A Demonstration of the Solid Platform for Social Web Applications. In Proceedings of the 25th International Conference Companion on World Wide Web (WWW '16 Companion). International World Wide Web Conferences Steering Committee, Republic and Canton of Geneva, CHE, 223–226. 2016. https://doi.org/10.1145/2872518.2890529
-
[15] W. Zhao, B. Zhou, C. Zhang, "Heterogeneous Social Linked Data Integration and Sharing for Public Transportation", Journal of Advanced Transportation, vol. 2022, Article ID 6338365, 14 pages, 2022. https://doi.org/10.1155/2022/6338365
-
[16] J. Werbrouck, P. Pauwels, J. Beetz and L. van Berlo. Towards a Decentralised Common Data Environment using Linked Building Data and the Solid Ecosystem. 2019.
-
[17] D. Henselmann, K. Kolinsky, S. Schmid, D. Schraudner, A. Both, and A. Harth, ‘Solid Proof of Concept in an Enterprise Loan Request Use Case’, 2022.
-
[18] X. Weng, H. Wu, Y. Pan and H. Chen, "Decentralized Personal Cloud Data Model and its Application in Campus Health Information System," 2021 IEEE Intl Conf on Dependable, Autonomic and Secure Computing, Intl Conf on Pervasive Intelligence and Computing, Intl Conf on Cloud and Big Data Computing, Intl Conf on Cyber Science and Technology Congress (DASC/PiCom/CBDCom/CyberSciTech), AB, Canada. 2021. doi: 10.1109/DASC-PICom-CBDCom-CyberSciTech52372.2021.00146.
-
[19] H. Chen, "Ubi-Care: a Decentralized Ubiquitous Sensing Healthcare System for the Elderly Living Support," 2019 IEEE Intl Conf on Dependable, Autonomic and Secure Computing, Intl Conf on Pervasive Intelligence and Computing, Intl Conf on Cloud and Big Data Computing, Intl Conf on Cyber Science and Technology Congress (DASC/PiCom/CBDCom/CyberSciTech), Fukuoka, Japan, pp. 543-547. 2019. doi: 10.1109/DASC/PiCom/CBDCom/CyberSciTech.2019.00108.
-
[20] Pandit HJ. Making Sense of Solid for Data Governance and GDPR. Information. 14(2):114. 2023. https://doi.org/10.3390/info14020114
-
[21] C. Sun, et al. ‘ciTIzen-centric DAta pLatform (TIDAL): Sharing Distributed Personal Data in a Privacy-preserving Manner for Health Research’. 1 Jan. 2023 : 977 – 996.
-
[22] Bailly, H., Papanna, A., Brennan, R. Prototyping an End-User User Interface for the Solid Application Interoperability Specification Under GDPR. In: Pesquita, C., et al. The Semantic Web. ESWC 2023. Lecture Notes in Computer Science, vol 13870. Springer, Cham. 2023 https://doi.org/10.1007/978-3-031-33455-9_33
-
[23] T. Theys and A. Bourgeus “The hardest thing is that we’re just doing things that have never been done before.” - Summary of a series of interviews focused on UX-related struggles and needs of designers and developers who are working with Solid Accessed: Sep. 25, 2023. [Online]. Available: https://solidlab.be/wp-content/uploads/2022/10/SolidLab_Flanders_UX_interview_results.pdf
-
[24] B.E.Penteado, J.C. Maldonado and S. Isotani. ‘Methodologies for Publishing Linked Open Government Data on the Web: A Systematic Mapping and a Unified Process Model’. 1 Jan. 2023 : 585 – 610.
-
[25] J. Sonnenholzner, ‘Grundsteuer-Erklärungen sorgen bei Eigentümern für Frust’, tagesschau.de. Accessed: Sep. 30, 2023. [Online]. Available: https://www.tagesschau.de/wirtschaft/verbraucher/grundsteuer-erklaerung-probleme-fristen-101.html
-
[26] ‘Reform der Grundsteuer’, Bundesministerium der Finanzen. Accessed: Sep. 30, 2023. [Online]. Available: https://www.bundesfinanzministerium.de/Content/DE/Standardartikel/Themen/Steuern/Steuerarten/Grundsteuer-und-Grunderwerbsteuer/reform-der-grundsteuer.html
-
[27] P. Archer, K. Smith and A. Perego Protocol for Web Description Resources (POWDER): Description Resources [Online] https://www.w3.org/TR/2009/REC-powder-dr-20090901/